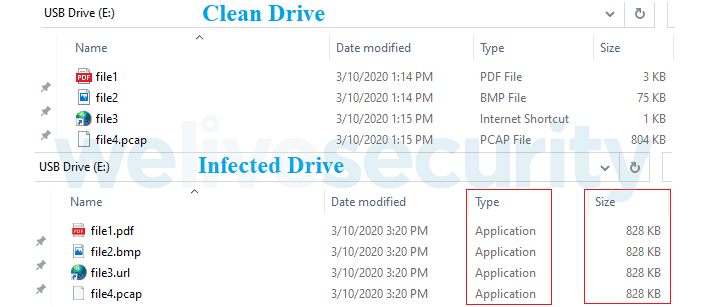
The botnet affected devices in Latin America, particularly Peru, are known as VictoryGate and active since at least May 2019, and have more than 90% of the compromised devices. After the C&Cs have been sunk, ESET security researchers have been able to estimate the size of botnet to over 35,000 computers. VictoryGate mainly focused on Monero mining, but the malware allowed the botmaster to issue node commands for downloading and carrying out additional payloads. So ESET believes that the intent of the botnet may at some point have changed. The botnet abuses the resources of infected crypto miners with a sustained 90-99% CPU load, slowing the system down and potentially damaging it. The botnet uses only infected removable devices for propagation. The malware copies all files on the USB drive to a secret root directory and uses fly-compiled Windows executables as obvious names. The USB drive is common to the victim, with all files and directories in order. The script starts both the assigned file and the initial module for the malware, which copies itself to a percentage of AppData and puts a shortcut in the startup folder to run at reboot. The malware will insert an AutoIt-compiled script into legitimate Windows processes to ensure communication and downloading and executing secondary payloads with the control and control (C&C) server. The script also checks for infecting attached USB drives. The bots may download and execute files, notify C&C of successful tasks, submit system information (username, hostname, installed antimalware product, AutomoIt version, and more), and tell C&C if the execution path is not the desired one. The downloaded payloads observed were AutoIt-compiled scripts trying to inject the XMRig mining program into the ucsvc.exe file. Next, the mining of the infected device begins. The botnet uses an XMRig proxy to mask the mining pool and avoids mining when the user opens Task Manager to conceal the use of the CPU. The cycle will be resumed once the Task Manager is closed. ESET reports that an average of 2,000 bots mining during the entire day and that a total of 80 Monero (approximately $6,000) have been produced by botnet operations.